ICS Shield Multi-Site Cybersecurity Solution
Description
ICS Shield is a top-down OT cybersecurity management solution for securing connected ICS/SCADA environments. This solution automates the deployment and enforcement of plant-wide security policies while focusing on security essentials such as inventory visibility, patching, log collection, remote access, and compliance ICS SHIELD SOLUTION reporting. Complying with the NIST Cybersecurity Framework, the NIST SP 800-82 guidelines, and leading international standards (including NERC CIP, ENISA, PERA, ISO 27001, and ISA/IEC-62443), ICS Shield improves the security compliance posture of industrial organizations.
ICS Shield helps you achieve an accurate inventory of your ICS assets including hardware, software, and service configurations. Automating this discovery process, ICS Shield enables end-to-end visibility of OT assets, empowering your organization to effectively enforce its security procedures. ICS Shield enables leading asset discovery technologies for optimized results.
In order to maintain high levels of security, uptime, and safety of distributed devices, secure remote access to field assets is required by first- and third-party personnel and machines. Providing extremely granular and robust AAA remote access, ICS Shield ensures secure remote access and monitoring, protected file distribution to devices, and safe data transfer from plants to HQ for analysis and risk management.
ICS Shield unifies and automates the policy management process, empowering the creation, deployment, and enforcement of plant-wide and granular security policies. Leveraging ICS Shield’s security policy management, operations, and control teams significantly improves OT cybersecurity and compliance.
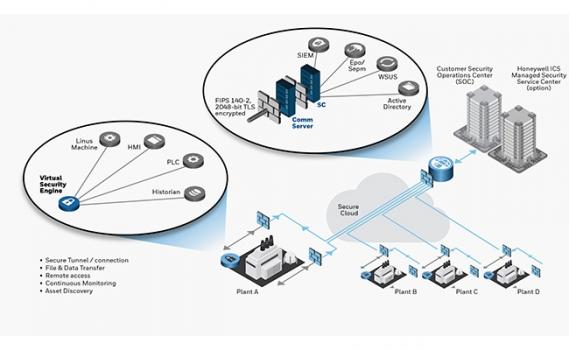
ICS Shield infrastructure is designed for multi-site, multi-vendor deployment, with all sites connected to the security and operations center via Honeywell’s Secure Tunnel. This distributed architecture guarantees data security and integrity. Policies and files are easily distributed through the Secure Tunnel from the Security Center (SC) located at the enterprise data center to the Virtual Security Engine (VSE) installed at each plant. Data collected from the ICS assets by the VSE is sent to the SC for reporting, analysis, and risk management purposes.
Specs
- Asset auto-discovery: Scheduling discovery of ICS assets for an up-to-date inventory
- Configuration collection: Collecting detailed data about each asset
- Asset classification: Classifying assets by their level of criticality
- Change management: Monitoring changes in asset inventory and configuration
- Asset visualization: Providing a clear view of all field assets by business and geography.
- AAA remote access: Including centralized authentication, granular authorization, and session accounting and control
- Password vault: Authenticating remote users without sharing device credentials
- Secure file distribution & data transfer: Securely distributing files to devices and sending data from devices to central security and operations center.
- Patching and anti-malware updating: Decreasing window of vulnerability between patch qualification and update
- Log collection: Empowering improved risk management
- Whitelists/blacklists: Hardening OT devices and reducing attack surface
- Securely move backup files to an offsite location improving incident recovery capabilities
- Custom policy creation: Enabling refining of organization’s cybersecurity
- Compliance reporting: Allowing compliance monitoring and the communication of identified vulnerabilities.
- Secure Tunnel: Powering secure communications using TLS encryption, with every session initiated outbound only using a single port and firewall rule.
- Security Center (SC): Serving as organizational security team’s main portal for top-down OT cybersecurity management and monitoring via an intuitive dashboard, while communicating with VSEs at plants and multiple IT security tools
- Virtual Security Engine (VSE): Enforcing policies and supporting a wide range of protocols for connecting to multiple assets
- Policy Manager: Powering the creation, deployment and enforcement of plant-wide granular policies and custom policies
- Reporting Tool: Generating customized and pre-defined compliance reports.