Manufacturing IoT Gets a Security Boost
Description
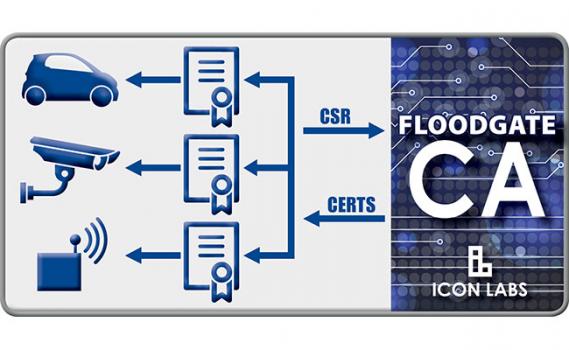
IoT security requires strong authentication measures to be effective. Floodgate Certificate Authority provides a closed PKI system that does not depend on public certificate authorities or third-parties to ensure all communication between known, trusted devices in the IoT are secure.
IoT security requires strong authentication. All IoT devices, including the smallest endpoints, must support mutual authentication, ensuring all communication is between known, trusted devices, and that all access is authorized. Certificate-based authentication using Public Key Infrastructure provides a proven, reliable authentication method.
The Floodgate CA can be deployed on a hardened server or hierarchy of servers in a private environment to provide a closed PKI system without dependence upon public certificate authorities or other third-parties. It can also operate as a sub-CA of a public CA, allowing OEMs to choose the operating model based on their IoT authentication requirements.
Floodgate CA can be used with any PKI client, including Icon Labs' Floodgate PKI Client Toolkit; an embeddable PKI client for IoT devices. Floodgate PKI Client enables even the smallest of IoT devices to generate keys, create certificate signing requests, and retrieve signed certificates from the Certificate Authority.
